Granting Full Disk Access to Malwarebytes
After publishing this post, Thomas Reed of Malwarebytes let me know there is indeed documentation on using a PPPC profile to enable full disk access. Thanks Thomas!
Malwarebytes has required full disk access on macOS Catalina and later since at least March 2020, but I only noticed recently as I was testing for Big Sur compatibility.
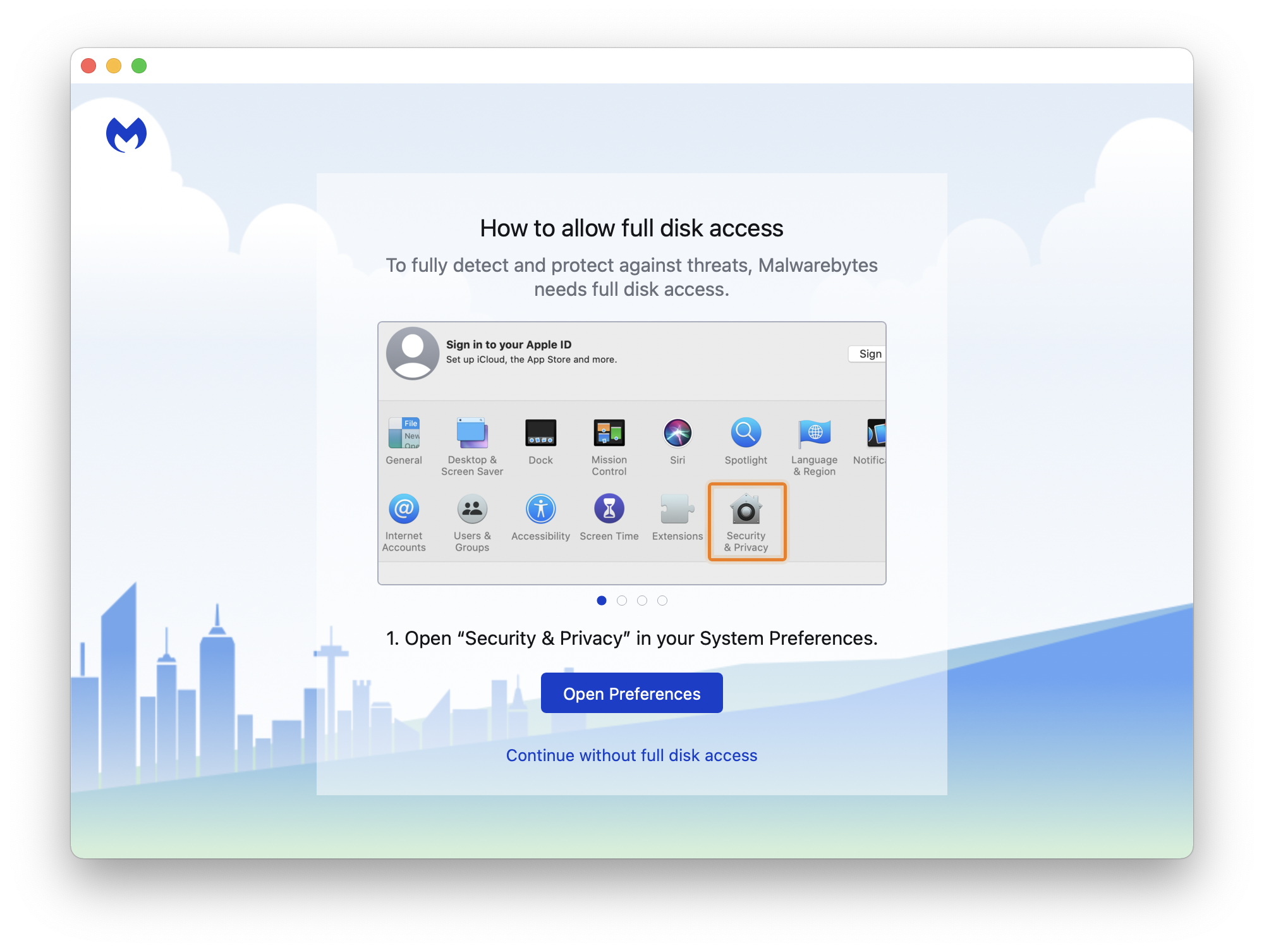
Their knowledge base offers this article showing the usual process of going to Security & Privacy > Privacy > Full Disk Access to check the box. However, since full disk access requires admin rights, I wanted to install a PPPC profile through MDM to pre-approve access for a standard user to run a Malwarebytes scan.
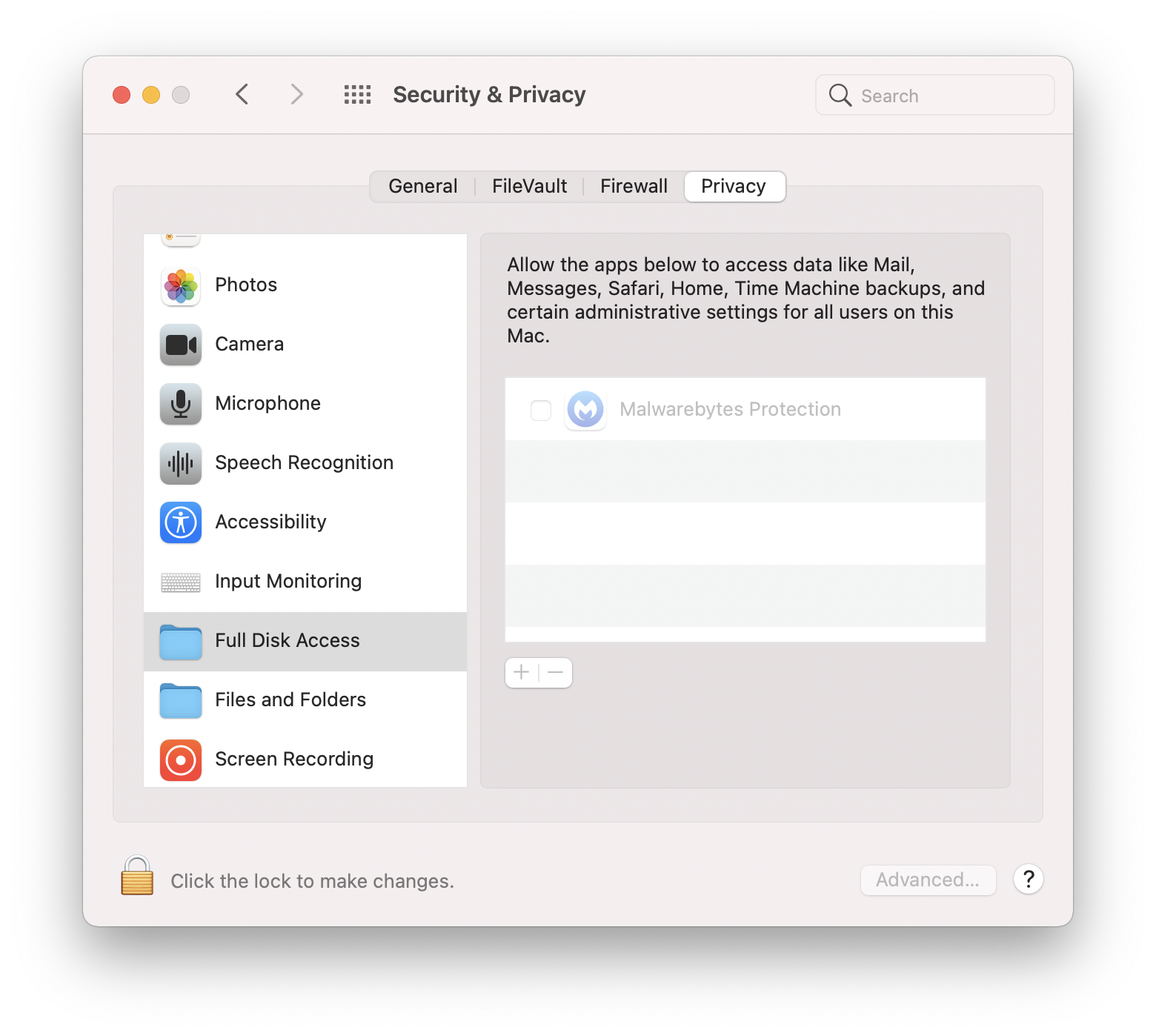
I noticed something unusual though. The app requiring full disk access isn’t the same one launched from Applications. Malwarebytes launched, Malwarebytes Protection wants access.

Typically it’s easy enough to find the bundle ID and code signing information for an app with which to generate a PPPC profile through PPPC Utility or directly through your MDM solution, but in this case the frontend Malwarebytes app calls Malwarebytes Protection to do the actual scan. There’s also no guidance from Malwarebytes to Mac admins on how to approve access through a PPPC profile. After a little digging it turns out Malwarebytes Protection is located at /Library/Application Support/Malwarebytes/MBAM/Engine.bundle/Contents/PlugIns/RTProtectionDaemon.app.
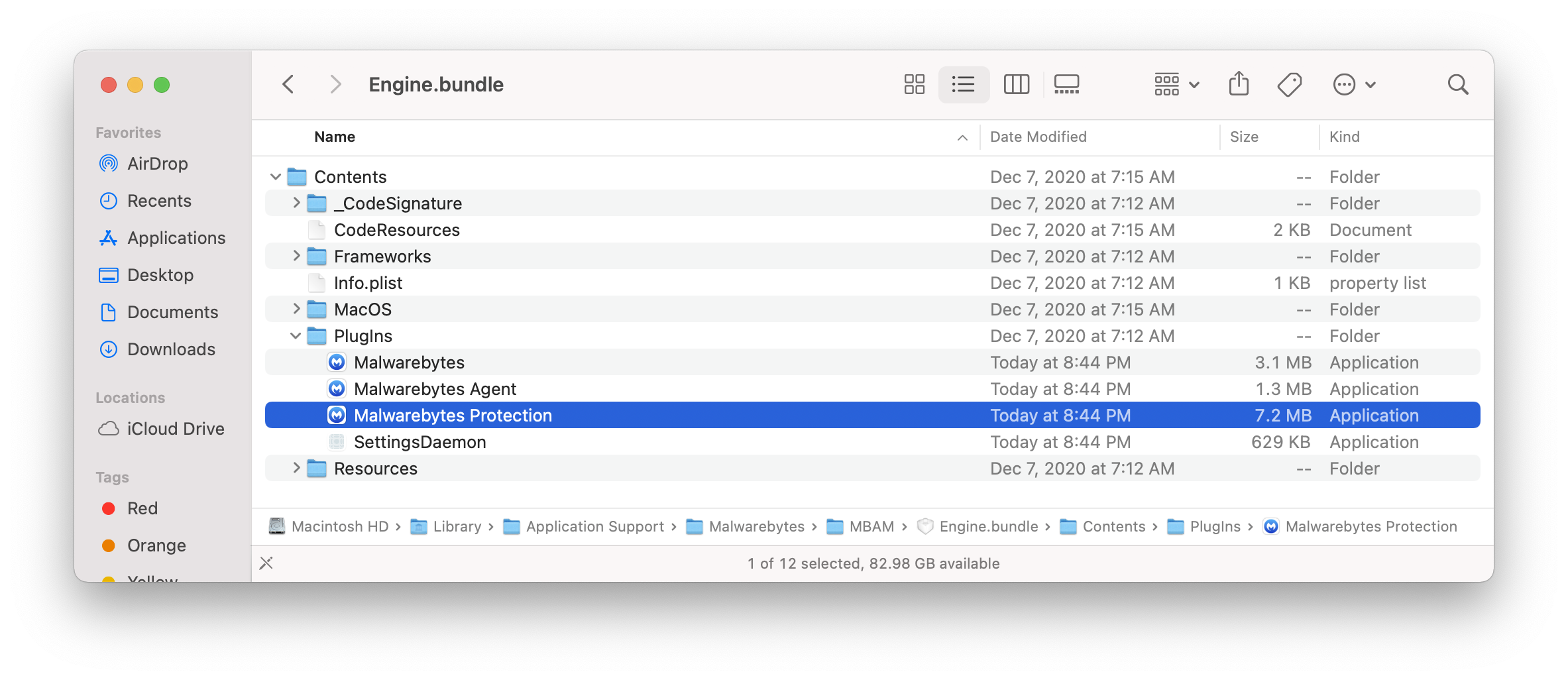
With that information in hand I was able to create a PPPC profile approving full disk access for Malwarebytes. It lives in my newly created mac-profiles repo which I plan to use for more examples like this.
https://github.com/nstrauss/mac-profiles
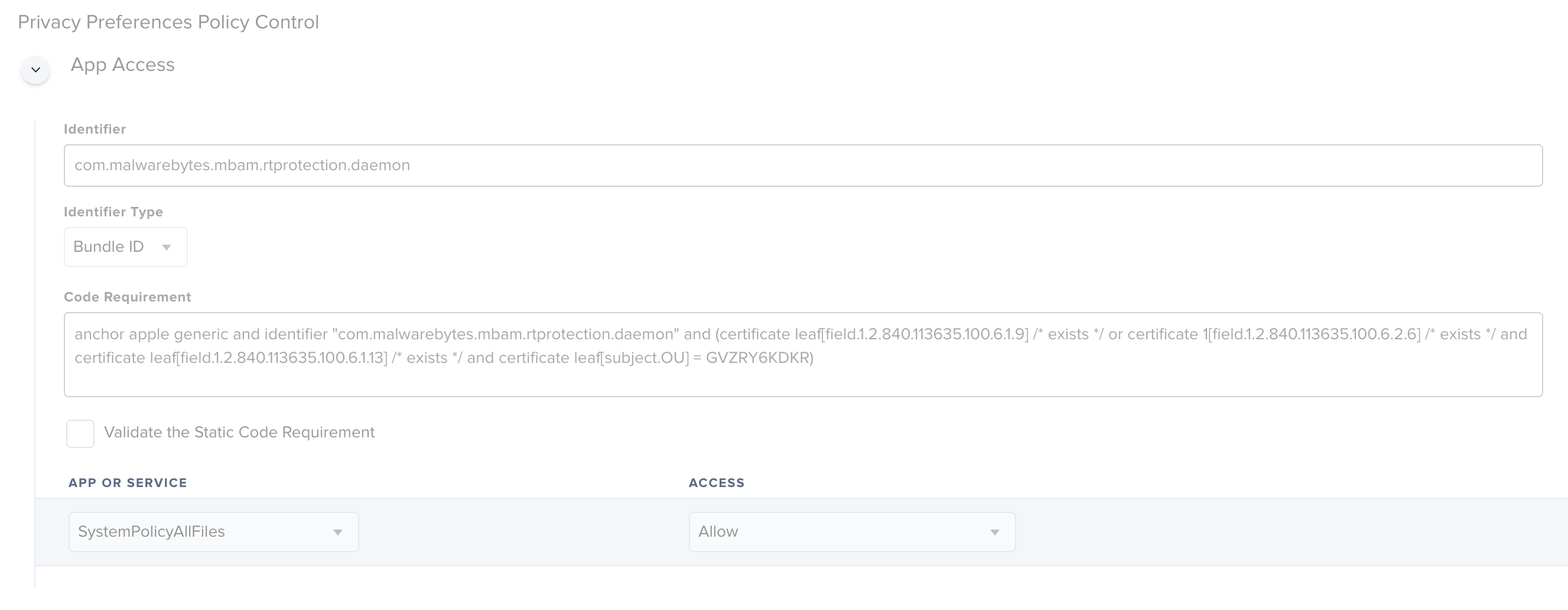
Jamf Pro admins can add a PPPC profile manually through Configuration Profiles > Privacy Preferences Policy Control by setting identifier to com.malwarebytes.mbam.rtprotection.daemon, SystemPolicyAllFiles to Allow, and code requirement to…
anchor apple generic and identifier "com.malwarebytes.mbam.rtprotection.daemon" and (certificate leaf[field.1.2.840.113635.100.6.1.9] /* exists */ or certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = GVZRY6KDKR)
In the future I’d like to see vendors provide example profiles or include information for IT admins to use their products in an enterprise setting. Too many are still keeping directions to standalone or consumer users.